主要是构造正确的payload
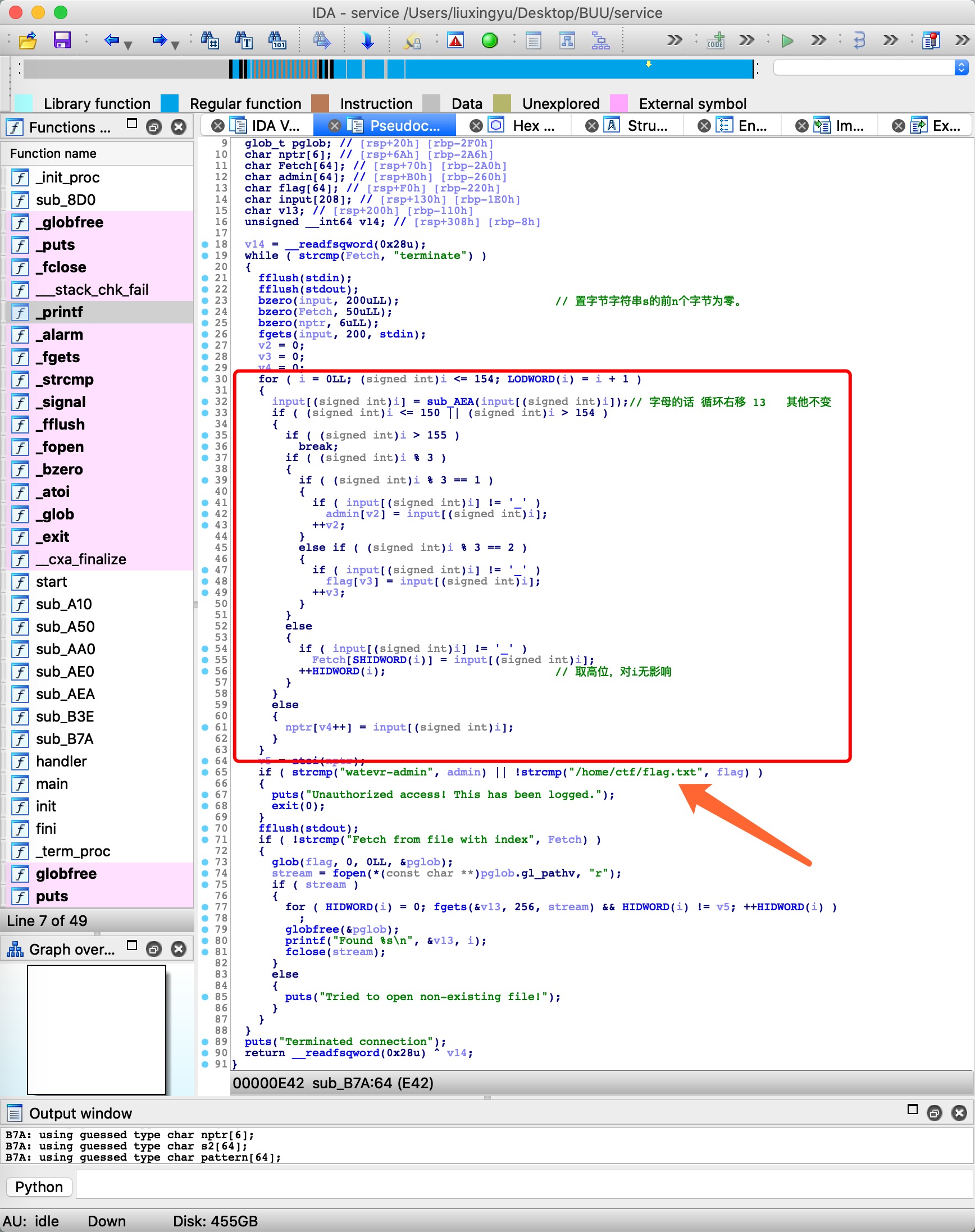
图里解释的很清楚了 这里说一下程序流程
首先把输入通过函数AEA处理一下,然后按照下标对3对模,分组,组合成新的字符串
模为0对部分字符串为’Fetch from file with index’
模为1对部分字符串为’watevr-admin’
模为2对部分字符串不能为’/home/ctf/flag.txt’
这里虽然说不能为这个路径,但是flag应该是在这个路径下,这里用多个/绕过
即字符串可以为 ‘/home/ctf///////flag.txt’
nptr在输入的151~153位的时候成为下面某个for的循环次数,这里控制为较小的数,比如0
满足所有条件后,该程序就会把该路径下的文件printf出来 即为flag
1 | from pwn import * |
